It’s a typical Monday morning. Coffee is brewing, emails are flying—until news of a data breach hits like a wrecking ball and shatters the routine.
Suddenly, the clock is ticking and the stakes couldn’t be higher. Tech teams race to contain the damage, in-house counsel scrambles to assess the breach's scope and legal implications, and insurers mobilize to mitigate fallout.
With regulatory deadlines looming and millions of records at stake, effective action hinges on having a solid cyber incident response plan—backed by reliable technology—already in place. Preparedness doesn’t just alleviate pressure and ensure peace of mind; it also provides your team with a steady foundation for your response. It isn’t just a comfort; it’s a responsibility.
And when every second counts, generative AI-powered data breach response solutions can rapidly comb through millions of documents to identify sensitive information with precision—potentially saving your business millions.
Your incident response team can use gen AI to help your organization prevent severe consequences from cyber attacks by following these five steps:
Step 1: Understand your core challenges and risk exposures
Step 2: Find the right tool with the Cyber Incident Response Solution Checklist
Step 3: Automate the entity list generation process for rapid identification and notification
Step 4: Secure success with responsible generative AI
Step 5: Evaluate the impact
But first, let’s look at how cyber incidents affect organizations worldwide, plus generative AI’s role on both sides of the aisle.
The Escalating Frequency and Cost of Cyber Crime
Despite the horror they inspire, cyber incidents are common, and they continue to become more prevalent. In fact, 72 percent of respondents to the Global Cybersecurity Outlook (GCO) survey reported a rise in cyber risks, according to World Economic Forum. And a notable 71 percent of chief risk officers anticipated severe organizational disruptions from cyber risks and criminal activity.
The immediate threat of a cyber incident is reputational damage, so a fast, accurate response is paramount. But more tangibly, cyber incidents are expensive. The US Federal Bureau of Investigation (FBI) estimates that losses resulting from cybercrime exceeded $12.5 billion in 2023. The global average cost of a data breach is a staggering $4.4 million, according to IBM’s Cost of a Data Breach Report 2025.
This is a 9 percent decrease compared to 2024—driven by faster identification and containment of the breach. The numbers confirm: breaches cost organizations millions, but fast, effective action can staunch the bleed.
Gen AI Usage in and Against Cyber Attacks
The rapid evolution of the cyber threat landscape is due, in part, to the rise of generative AI. It’s not just transforming cyber incident response; it’s a weapon that attackers can use, too. According to IBM’s research, 16 percent of data breaches involved AI-driven attacks in 2025: with 37 percent involving AI-generated phishing and 35 percent involving AI deepfake attacks. It takes malicious actors a miniscule 5 minutes to craft a convincing email using gen AI, compared to around 16 hours manually.
On the other side, organizations are leveraging generative AI to fortify their defenses against these attacks and augment their response. And the numbers support the financial and security benefits of these solutions:
Gen AI Usage in Cybersecurity and Cyber Incident Response |
||
|
97% of organizations reported an AI-related security incident and lacked effective AI access controls. |
32% of organizations extensively leverage AI security and automation. 40% are leveraging AI on at least a limited basis. |
1 in 3 security teams used AI and automation evenly across cybersecurity workflows, including: prevention, detection, investigation, and response. |
|
72% of organizations used AI and automation to respond to a data breach. |
Security AI use yields 34% lower cost of breach. |
$1.9M cost savings from extensive use of AI in security, compared to organizations that did not use AI. |
Now, let’s get into how your cyber incident response team can leverage gen AI.
Step 1: Understand Your Core Challenges and Risk Exposures
Vijay Rathour, Partner, Digital Forensics and Cyber Investigations Group at Grant Thornton UK, describes breaches as a “multi-headed hydra, with new vulnerabilities popping up one after another” and a to-do list that multiplies at every turn.
While every breach is different, the majority share similar core difficulties for the teams on the front line:
- Struggle to manage large volumes of highly complex, sensitive data
- Manual, labor-intensive workflows
- Fragmented tool ecosystems, plus data movement and privacy risks
- High resource demands and cost constraints
- Limited automation and scalability
- Reviewer experience and turnover risk
- Searching for the unknown
- Under pressure to deliver quality response in short timeline—at the risk of significant fines and additional legal action
- Need to keep up with complex, evolving privacy laws
Once the impacted data has been identified, incident response teams need a tool that runs through this data as quickly as possible to determine if sensitive information exists, and, if so, link it to the right people.
This gives teams the answers they need to act—solving these challenges proactively so they can focus their attention on higher-value work. AI-powered workflows consistently achieve these results in less time and with greater accuracy than manual review. (More on this later.)
So having a reliable solution already in place gives response teams a competitive edge when an attack hits.
Step 2: Find the Right Tool with the Cyber Incident Response Solution Checklist
So how do you know which solution to choose?
Reliable data breach response solutions have five key attributes:
- Defensibility
- Efficiency
- Accuracy
- Security
- Scalability
They also offer measurable outcomes:
- Reduce labor costs
- Increase operational efficiency
- Provide flexibility to meet client demands
- Enhance review accuracy and response time
- Simplify workflows
- Integrate with existing legal/case management systems
Solutions must protect client data while facilitating fast, secure access to that data. They also can’t be a black box. If you can’t explain the tool to stakeholders, it’s not useful.
Finally, when evaluating the effectiveness of a tool, consider a 95/5 principle: a solution may aptly handle the 95 percent of easy documents. But how is it built to address the edge cases: complex, difficult docs like W-2s, handwritten doctor forms, et cetera?
Step 3: Automate the Entity List Generation Process for Rapid Identification and Notification
Quickly building your entity list so you can notify affected parties in a timely manner is the first step to restoring trust in your organization. But without generative AI-powered tools like Relativity Data Breach Response, breach review is time-consuming and labor-intensive. Teams spend hours sifting through data to find sensitive information, linking that data to an individual, and assembling defensible reports—often delaying critical updates and reporting.
But how does gen AI-powered incident response work? When a cyber incident strikes, breach response tools reduce the volume of documents that require manual review. They triage your data set, flag PII, and automatically link personal information to entities (individuals or subjects). This minimizes costs, mitigates legal risks, ensures compliance, and enhances accuracy, while shrinking the timeline between breach and notification.
Here’s a quick breakdown of how it works:
- Reviewer selects applicable types of personal information and runs data analysis.
- Data Breach Response analyzes documents, identifies PI & PHI, and links entities to create the initial entity report.
- Reviewer QCs documents and make any edits required.
- Data Breach Response auto-deduplicates, and the reviewer checks for entity conflicts before moving forward with the final entity report.
So how does that translate into results? In one large-scale breach response KPMG performed for a restaurant chain client, Data Breach Response culled 1.5 terabytes of data by 90 percent—trimming 1 million documents down to 100,000 and 15 million breach records to review to only 150,000. And the tool consistently delivers 90+ percent recall and low false positive rates.
That’s evidence of a pretty significant improvement over manual review.
Step 4: Secure Success with Responsible Generative AI
The question at the forefront of AI discourse: how do you use gen AI responsibly in a cyber incident? The answer is simple: human oversight is essential for ensuring successful outcomes with AI-driven systems.
The streamlined workflows of tools like Data Breach Response drastically reduce manual workload—allowing for more time for thorough QC.
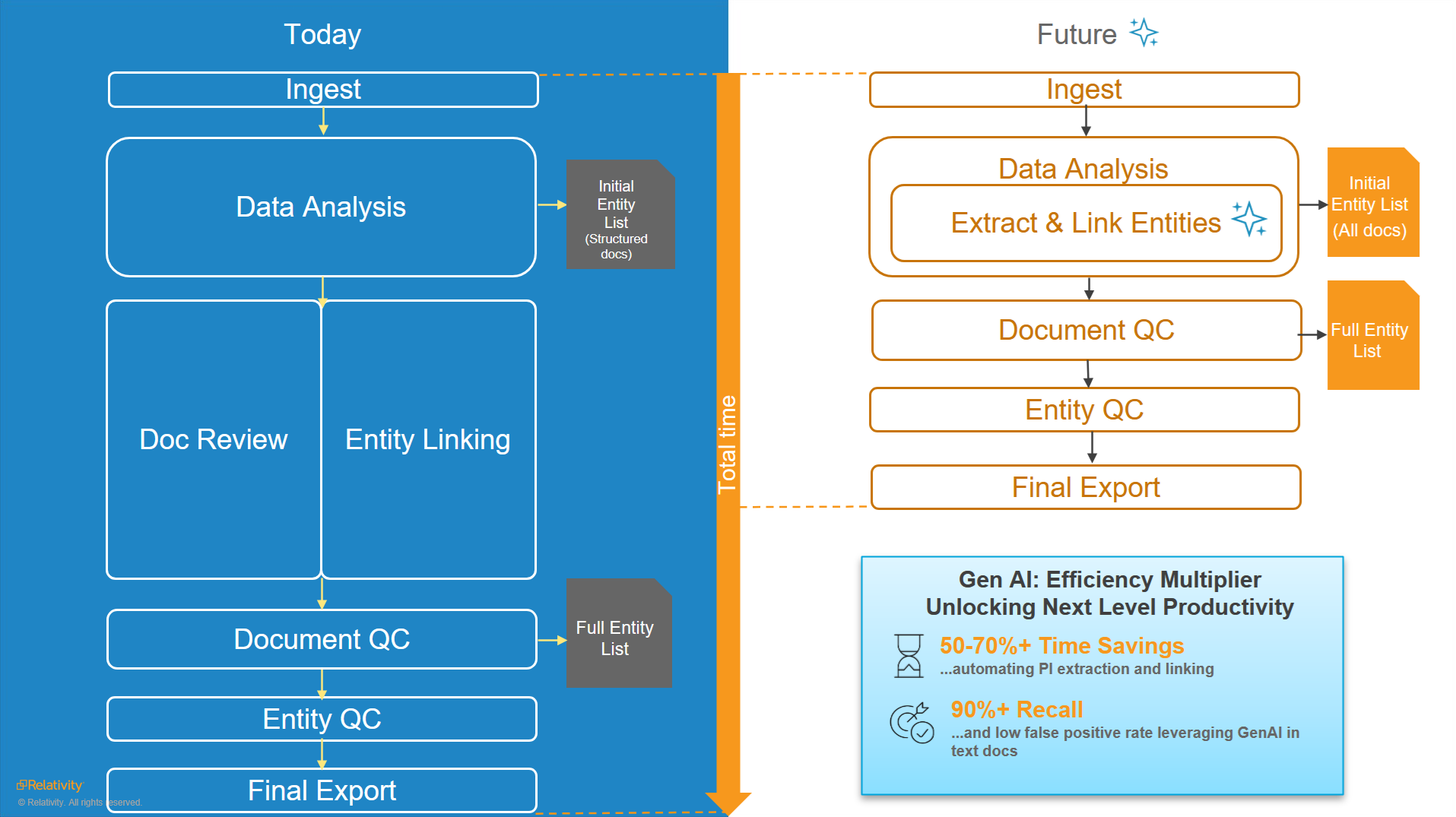
As Alanna Dent, product manager at Relativity, explains: “It is both a reduction in time and a reduction in steps. Both the initial impact report and the final entity list come earlier in the process. Today's workflow (pictured below) gets you just the full entities from structured docs during Data Analysis. With gen AI, you get entities from both structured and unstructured docs with your first job run. And then you get your final report ready for entity QC far earlier in the overall timeline.
“You’ll need fewer reviewers doing the manual, time-intensive review, as the primary focus will turn to QCing the AI-detected and linked entity list.”
Meaning your team can confidently—and responsibly—validate your results.
Step 5: Evaluate the Impact
What does gen AI-backed cyber incident response look like in action? And what impact does this have on the business? Let’s take a look at how gen AI tools perform when a crisis hits.
When service provider Morae was faced with tens of thousands of documents to review for a client breach, they brought in AI-powered Data Breach Response to automatically identify documents likely to contain personal information. This cut the scope by 79 percent and eliminated time wasted on irrelevant content—resulting in a 33 percent increase in review speed, stronger accuracy, and a more efficient, focused team.
“Integrating GPT-powered AI into Data Breach Response, plus the full scale of the RelativityOne platform, transformed our workflow efficiency, saving us significant review time. We were able to deliver faster time to insight with the added leverage of GPT and maintain our defensible outcomes for our client—ensuring they navigate breaches with greater confidence,” said Josh Franks, cyber practice lead at Morae.
“This technology is not just an enhancement; it’s a strategic necessity for managing the increasing volume and complexity of data breaches. We were able to leverage our team as a vehicle of validation instead of the grind of full-scale manual extraction or through processes that live outside the RelativityOne environment.”
“I pulled the stats for a project we’re doing with a review team of five. In one week, Data Breach Response saved 680 hours of work.” – associate director of e-discovery at a professional services company
Documenting this kind of ROI to share among internal stakeholders can help you build buy-in on tech and training investments, ensuring your team stays up to speed with ongoing innovations in the cybersecurity space. Of course, it also makes a compelling argument when you’re pitching your use of the technology to clients and other teams who may not know much about it.
Key Takeaways for Using Gen AI in Cyber Incident Response
Cyber incidents are overwhelming, but generative AI allows teams to respond faster and more accurately than ever. By building the entity list in a fraction of the time, breached organizations can promptly notify affected parties to remain compliant and transparent.
The truth is, data breaches are personal. It’s not just nebulous data that’s exposed. It’s your son’s date of birth. Your grandmother’s social security number. When minutes matter, responding responsibly doesn’t just mediate damage for the breached organization; it also protects real people and helps them trust your business again.
But cyber incident responses don’t have to be their own kind of catastrophe. Wrangle the power of generative AI and take back your data strategy—responsibly.
Graphics for this article were created by Caroline Patterson.












